AWS IoT Secure Tunneling: Access & Manage Remote Devices | SSH
Are you ready to unlock the power of secure, remote access to your IoT devices? By leveraging AWS IoT Secure Tunneling, you can establish robust, bidirectional communication without the complexities of firewall adjustments or cumbersome control messages.
The landscape of the Internet of Things (IoT) is rapidly evolving, with businesses across industries deploying an ever-growing number of connected devices. The ability to securely access and manage these devices remotely is paramount, enabling efficient monitoring, troubleshooting, and maintenance. Traditionally, this has involved methods such as sending control messages via MQTT topics or updating device shadows, which can be complex to implement and manage. AWS IoT Secure Tunneling offers a streamlined solution, providing a secure, remote access solution that directly integrates with AWS IoT, allowing you to access your IoT devices from anywhere.
| Feature | Details |
|---|---|
| Technology | AWS IoT Secure Tunneling |
| Purpose | Provides secure, remote access to IoT devices. |
| Key Benefits |
|
| How it works |
|
| Implementation |
|
For more detailed information on AWS IoT Secure Tunneling, please refer to the official documentation on the AWS website. This documentation provides comprehensive guidance on setting up and utilizing secure tunneling for your specific IoT device management needs.
- Alice Rosenblum Onlyfans News Leaks Latest Updates
- Alice Rosenblum Onlyfans Latest Leaks Updates Whats Trending
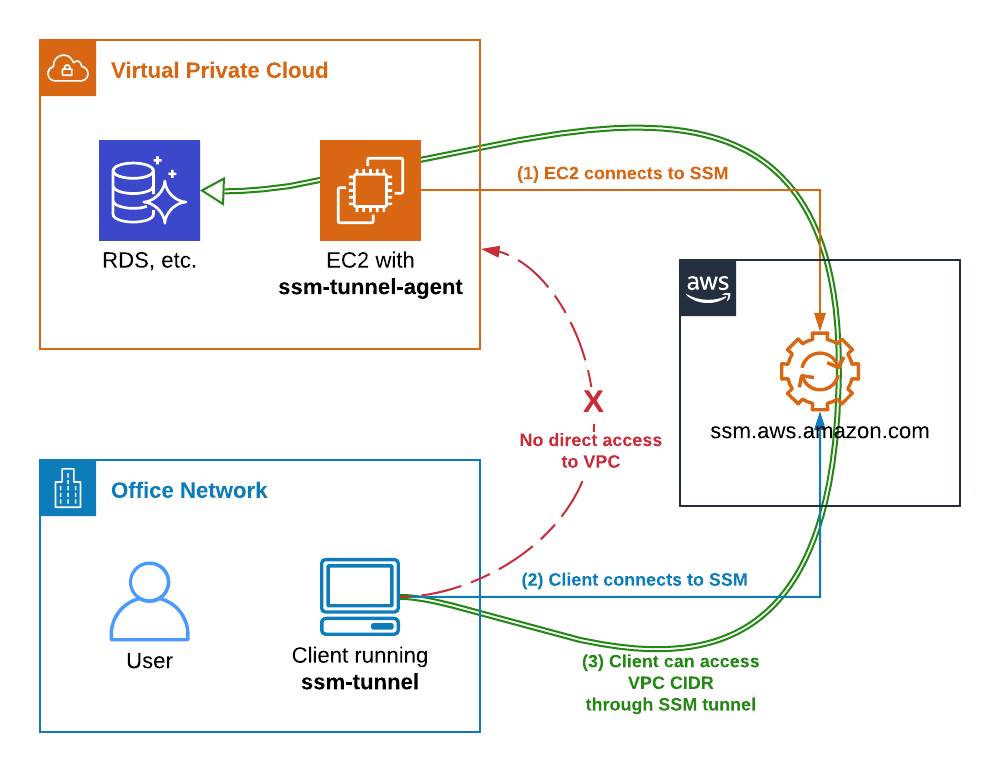
One of the key advantages of AWS IoT Secure Tunneling is its ability to bypass the complexities of traditional remote access methods. Instead of having to manipulate firewall rules or manage custom control message protocols, you can establish a secure connection with minimal effort. AWS IoT Device Management is a suite of tools designed to help businesses build IoT applications across industries. AWS IoT Secure Tunneling integrates seamlessly with this ecosystem, simplifying remote access to your devices. With secure tunneling, you can easily monitor device anomalies, take mitigating actions, and rectify the device state where needed, all while maintaining the same security level provided by firewall rules at a remote site.
Imagine you are working with a remote device called "remotedevice1". You've set it up using either the manual setup method or the AWS IoT API. With AWS IoT Secure Tunneling, you can now access it securely from anywhere. To achieve this, you'll need to utilize a software proxy that runs on both the source and destination devices. This proxy acts as a secure relay, managing the flow of data between your device application and the secure tunnel. The AWS IoT agent snippet is a valuable resource for further understanding how the process works, providing detailed information on integrating the local proxy.
To begin setting up your IoT device, the first step is to configure the "destination device" which in this case is your Macbook. The process leverages the power of the AWS Cloud. The AWS IoT service provides a robust and secure means of establishing this connection. The process typically involves creating an SSH tunnel that connects a device on the AWS (the source) to your Macbook (the destination). After successfully creating the tunnel using IoT Core, you will receive the access tokens that are essential for secure communication.
- Inigo Montoya Quotes Story Behind The Princess Bride Legend
- Hannah Barron Nudes Leaks Latest Pics Videos Dont Miss
After the tunnel is open, you can download a 'cat' file for the source device. This 'cat' file is crucial; you can use it to start the local proxy in source mode, which then connects the source side of the tunnel. It is also possible to specify a timeout period for the credentials. It's usually recommended to keep this timeout relatively short. This way, if your access tokens were somehow leaked, their validity would expire naturally, reducing potential security risks. This feature significantly simplifies the onboarding process. Customers no longer have to compile and install a local proxy on the operator's device.
To use this feature, you will need to create an IoT thing in the AWS IoT registry. For example, create a thing called "remotedeviceA". Then, you will be able to create a tunnel through the AWS IoT console. It is also possible to create tunnels directly from the AWS IoT console or from the details page of the created IoT thing. When creating a tunnel from the tunnel hub, you can select whether to use the quick setup or the manual setup method. After the tunnel is created, you can move to the tunnel hub of the AWS IoT console, select the tunnel you have created and display its details. Then, open the [secure shell (ssh)] session and select [connect] to start a remote session.
Let's delve into the process of establishing a connection using AWS IoT Secure Tunneling and secure shell (SSH) on a deeper level. The method supports SSH authentication via private keys. This feature allows for easier device anomaly monitoring. Additionally, this capability allows you to easily rectify your device's state where needed. AWS IoT Secure Tunneling supports "private key" SSH authentication, making it easier for you to monitor device anomalies, take mitigating actions, and rectify the device state where needed. This method provides a secure, remote access solution that directly integrates with AWS IoT, allowing you to access your IoT devices remotely from anywhere. This feature eliminates the need for complex configurations, streamlining the onboarding and management of your devices.
After a tunnel is open, AWS IoT device management provides the "cat" for the source that you can download on the source device. You can use the "cat" to start the local proxy in source mode, which then connects the source side of the tunnel. For more information about local proxy, see local proxy.
To delete a tunnel, you can go to the Tunnels hub in the AWS IoT console, select the tunnels you want to delete, and choose "Delete tunnel." Alternatively, you can use the AWS IoT API to delete a tunnel using the "CloseTunnel" API operation. This gives you flexibility in managing tunnels whether you're operating through the console or programmatically.
The AWS IoT console allows you to navigate the tunnels hub. You can select the tunnel you've created, view its details, and initiate an SSH session. Launching the local proxy (in destination mode) is integrated with AWS management console. Then, connect and register the device.
AWS IoT Secure Tunneling supports several key features and settings that contribute to its effectiveness. One critical aspect is the ability to set a timeout on the access tokens. It's highly recommended to keep this timeout relatively short. This practice minimizes the potential damage if the access tokens are compromised. This setting ensures that tokens expire naturally, thereby reducing the window of vulnerability.
Beyond creating the tunnel, an important part of the process is configuring your devices to communicate through it. This involves deploying and configuring the software proxy. This proxy acts as a bridge between the device application and the secure tunnel, ensuring secure bidirectional data flow. The correct configuration of the proxy is essential for the secure exchange of information and the proper functioning of the remote access.
By leveraging AWS IoT Secure Tunneling, you gain a secure, scalable, and efficient method for remote access. The integration of the feature within the existing AWS ecosystem makes it easy to implement. As a result, you can achieve a secure remote access solution that helps streamline device management. Using secure tunneling is an excellent approach to setting up and maintaining secure connections to your devices.
Article Recommendations
- Unveiling Kristi Noem From Bedhead To Bikini Buzz Latest Updates
- Egyptians Beliefs Lifes Most Significant Pursuit Discover Now

Detail Author:
- Name : Elfrieda Powlowski
- Username : eli.schmidt
- Email : olson.antonetta@hotmail.com
- Birthdate : 1999-07-23
- Address : 601 Aric Union South Velmaville, NH 79476-3456
- Phone : 1-863-625-9582
- Company : Mitchell PLC
- Job : Photographic Processing Machine Operator
- Bio : Praesentium repellat sapiente et itaque. Quae doloribus libero ducimus sint qui quidem. Accusantium aut quaerat quidem dicta et soluta at.
Socials
instagram:
- url : https://instagram.com/khauck
- username : khauck
- bio : Ea qui optio fuga vero. Id ut voluptatem aperiam dolor at atque.
- followers : 1858
- following : 217
twitter:
- url : https://twitter.com/khauck
- username : khauck
- bio : Inventore officia quo facere. Dolores aspernatur est alias enim fugit error.
- followers : 548
- following : 2347
tiktok:
- url : https://tiktok.com/@karine_official
- username : karine_official
- bio : Earum nihil ea consequatur at. Eaque eos et mollitia commodi.
- followers : 2972
- following : 1916
facebook:
- url : https://facebook.com/khauck
- username : khauck
- bio : Velit magni laboriosam ut dolorum enim quam.
- followers : 2977
- following : 1862
linkedin:
- url : https://linkedin.com/in/karine.hauck
- username : karine.hauck
- bio : Velit quo voluptatum officia eum illum tempora.
- followers : 2673
- following : 369