IoT SSH Login: Username & Password Security - Your Complete Guide
Are your Internet of Things (IoT) devices as secure as you think? Securing access to your IoT devices through SSH login is not just a best practice; it's a necessity in today's interconnected world. This article delves into the essential aspects of SSH login for IoT devices, providing a comprehensive guide to managing usernames, passwords, and securing your valuable connected devices.
The modern landscape is populated with a myriad of IoT devices, from smart home appliances to industrial sensors, each presenting a potential entry point for malicious actors. The security of these devices hinges on robust access control, and SSH (Secure Shell) plays a pivotal role in achieving that.
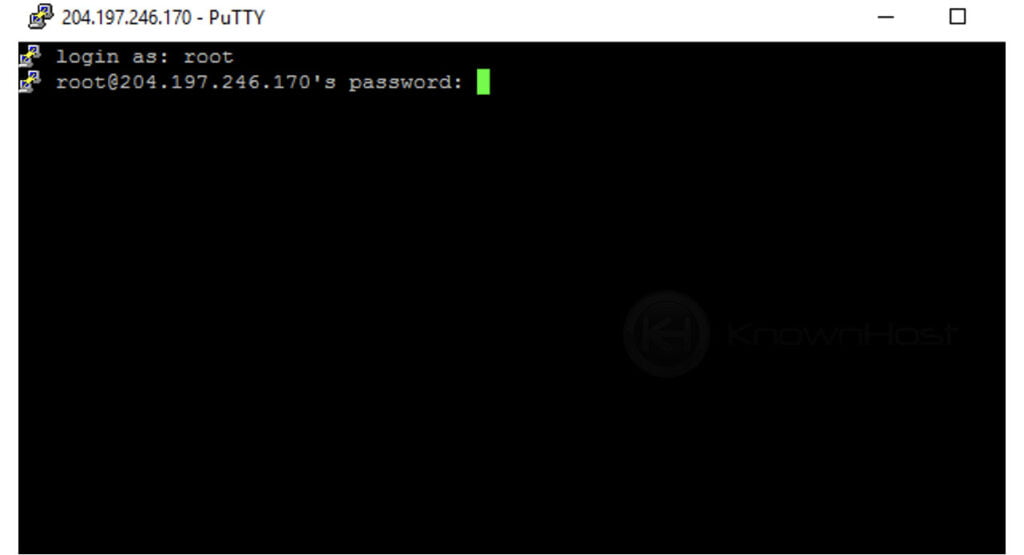
To establish an SSH connection, you'll initiate the process by utilizing an SSH client. This client, available on virtually any operating system, allows you to securely connect to your IoT device. The initial step involves entering the device's IP address, alongside your designated username and password or, for enhanced security, an SSH key for authentication. Correctly configuring these elements is paramount; it's the gateway to managing and controlling your device remotely.
Once the connection attempt is made, the SSH client will reach out to the IoT device. If everything is configured accurately, a secure connection will be established, creating a private communication channel. This channel encrypts all data exchanged between your client and the device, safeguarding sensitive information from prying eyes. This encryption is a core aspect of SSH's security, protecting against eavesdropping and data breaches. Subsequently, you will be prompted to authenticate the connection, which typically involves entering your password or providing an SSH key, depending on the configuration.
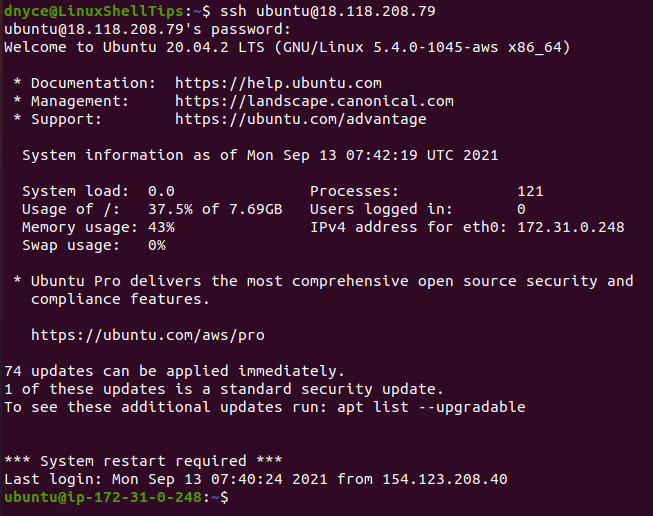
Let's consider a practical scenario: You have a Raspberry Pi running Ubuntu Core, and you've configured it to accept SSH connections. To connect, youd open your SSH client, and enter the Pi's IP address. Then, you would specify the username, often 'ubuntu' or 'root,' along with the appropriate password. After that you will gain access to the command line. The same principle applies to other devices, such as Dragonboards or Minnowboards. The key is to know the correct credentials.
For IoT devices, the default credentials can often be a point of vulnerability. Many devices come pre-configured with default usernames and passwords, which are readily available online. Leaving these unchanged is akin to leaving your front door unlocked. Immediately changing the default credentials to strong, unique passwords, or utilizing SSH keys is a crucial step.
SSH keys offer a significantly more secure alternative to passwords. They rely on cryptographic key pairs: a private key, kept secret, and a public key, which is placed on the device. When you attempt to connect, your client uses the private key to authenticate. This process is much more resistant to brute-force attacks and password cracking.
Consider an example to highlight the significance of SSH keys. You've set up a Raspberry Pi and want to access it remotely. Instead of using the default "pi" username and "raspberry" password (an extremely insecure default), you generate an SSH key pair on your computer. You then place the public key on the Raspberry Pi, and only the private key is needed to authenticate. This way, if someone intercepts your connection, they won't gain access to the device, as they do not have your private key.
When configuring your IoT device for SSH, you may need to utilize specific commands. For instance, you might employ the `ssh` command to connect, followed by the username and the device's IP address: `ssh user@192.168.1.100`. If prompted, enter the password or, if configured, use the SSH key.
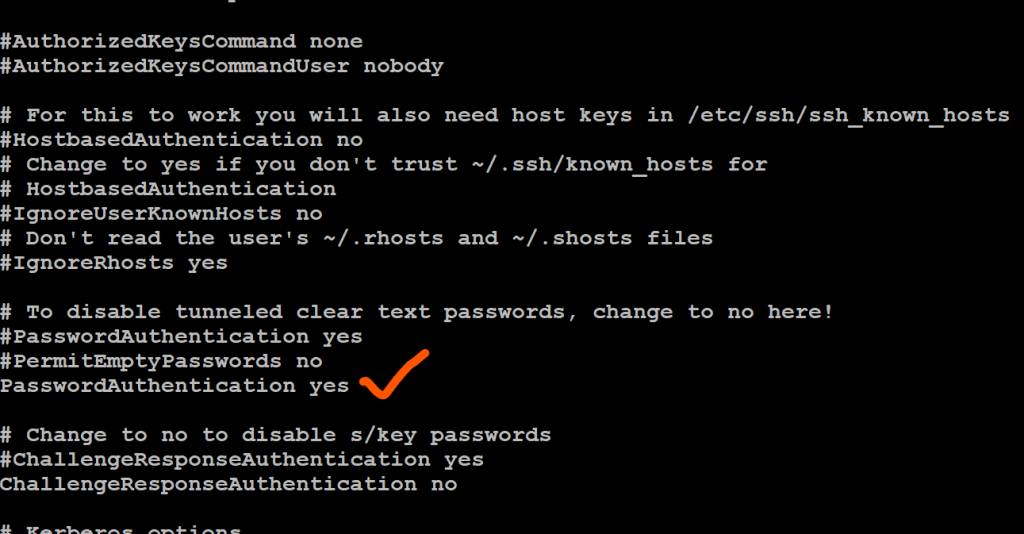
Sometimes, you might need to modify the SSH configuration. This could involve changing the default SSH port (port 22) to a custom one, which is a security best practice. This makes it more difficult for automated scanners to find your SSH server. Additionally, you can disable password authentication altogether and enforce SSH key authentication only, substantially improving security.
However, security isn't limited to strong passwords or SSH keys. It extends to port management. Many IoT devices utilize port 22 for SSH. Changing this default port is an important security measure. By changing the default SSH port to something non-standard, you effectively hide your SSH server from casual port scans. This is like having a hidden entrance to your home.
Now, lets discuss practical examples. For example, with a Raspberry Pi, you will typically use the username "pi" and the password "raspberry" (if you haven't changed it). To connect via SSH, you'd use the command `ssh pi@`. A similar concept applies to other devices, such as Banana Pi, where you might use "root" as the username. In cases like Ubuntu Core, the IP address is usually displayed on the console, meaning you would SSH into the device. It is vital to know the devices login details or configure them as instructed.
Security is paramount, however. Consider a situation where the default OpenSSH configuration on a Windows machine does not allow login without a password. In such a case, you would need to change the default OpenSSH configuration to work without passwords. Alternatively, you could create a login that has a password.
For remote access to your devices, consider solutions like SocketXP. These tools provide a secure, alternate method to connect to your IoT device's SSH server, adding a layer of protection against threats. Furthermore, brute-force attacks on SSH significantly outpaced attacks against telnet, making it a major vector for compromise.
Let's explore a real-world scenario. You've configured Ubuntu Core on a Raspberry Pi 3, but you cannot recall your username and password. In such cases, you might consult documentation, or seek community support, to determine the default credentials or the process to reset them. You need to confirm the SSH interface is enabled, which is often achieved after a default password is changed.
Remember that changing default passwords and usernames or using SSH keys is an essential component of a robust security posture. Always avoid using default credentials. A common attack strategy is brute-forcing passwords using wordlists, such as those built from previous botnets. Taking steps like key-pair generation, setting a custom port, and monitoring your SSH logs provide much more security.
To make the process easier, you may utilize a solution like Clarkwang/passh, which works on MacOS and Linux, which can help you to automate the process for logging into your devices.
The key to secure SSH login on IoT devices lies not just in understanding the technicalities, but in a proactive security mindset. Secure your credentials, implement multi-factor authentication if possible, and always be vigilant against potential vulnerabilities. By following these guidelines, you can fortify your IoT devices against unauthorized access and protect your digital assets.
In order to successfully connect to your IoT device using SSH, you need an SSH client. Popular options include PuTTY for Windows, and the built-in terminal on macOS and Linux. You will then enter the IP address, user name, and then the password when prompted.
Many devices come with their own default credentials. For example, to connect to a Raspberry Pi, you would enter "pi" as the username, and "raspberry" as the password (or your changed version). Always change the default credentials immediately after setting up the device, to protect against unauthorized use.
If you've done everything correctly, you should be prompted to enter your SSH password. Once entered, you gain access to the device, enabling you to configure and manage it.
Article Recommendations
- Alice Rosenblum Watch Discover Cam Leaks Hot Content
- Alice Rosenblum Leaked Content Onlyfans Updates Watch Now
Detail Author:
- Name : Elody Brekke
- Username : nharris
- Email : aconnelly@hotmail.com
- Birthdate : 1994-01-06
- Address : 49164 Ullrich Ranch Apt. 322 South Casandramouth, LA 04051
- Phone : 910-676-8327
- Company : Herzog Group
- Job : Earth Driller
- Bio : Accusamus dolor impedit unde rerum quibusdam. Necessitatibus quia ratione commodi dolorum dolorem. Veniam autem facilis sapiente aut facilis aut maiores sequi.
Socials
linkedin:
- url : https://linkedin.com/in/waelchil
- username : waelchil
- bio : Ut soluta odit nam suscipit omnis aut.
- followers : 1695
- following : 1763
twitter:
- url : https://twitter.com/luisa.waelchi
- username : luisa.waelchi
- bio : Saepe fugit voluptas qui nulla temporibus. Laboriosam et ut accusantium odit. Voluptatem qui eos sit. Soluta odit quos quod quam aliquam fuga qui.
- followers : 5297
- following : 2172
tiktok:
- url : https://tiktok.com/@luisa.waelchi
- username : luisa.waelchi
- bio : Eos amet necessitatibus cumque illo repellat et.
- followers : 6869
- following : 2102
instagram:
- url : https://instagram.com/luisa.waelchi
- username : luisa.waelchi
- bio : Cum reiciendis recusandae et provident quasi omnis. Id aut repudiandae rerum suscipit quae dolores.
- followers : 2190
- following : 1208